Discover TPM 2.0’s technical role in Windows’ security framework, its integration in Windows 11, and hardware implications.
If you are a Windows PC user or a gamer, you must have come across the term TPM 2.0 at some point. TPM 2.0 stands for Trust Platform Module version 2.0. Nowadays, certain applications and games, like Valorant, require TPM 2.0 to be enabled in order to run them properly.
But what exactly is this technology? And more importantly, what does it do? In this post, let us talk in-depth about TPM 2.0 on Windows. Let’s dive right in.
What is TPM 2.0?
On Windows, TPM 2.0 is essentially a dedicated hardware chip embedded into most modern setups. It gained popularity with the release of Windows 11 and serves as a central security requirement. Sensitive data, such as encryption keys, passwords, and biometric information, is saved on this chip in an isolated and secure environment.
TPM 2.0 handles cryptographic functions independently of the operating system. In doing so, it ensures that key security tasks, like software integrity verification and managing secure boot processes, are performed without any hitches.
What Does TPM 2.0 Do in Windows 11?
TPM 2.0 is an integral part of the security architecture of Windows 11. The hardware chip is mainly used for the following tasks:
- Secure Boot- Ensures that the system boots only trusted software.
- Data Encryption- Helps manage cryptographic keys. These keys are responsible for the protection of data stored on the computer.
- Hardware-based Authentication- Is responsible for enhancing features like Windows Hello by the secure storage of biometric information.
By implementing these functions, TPM 2.0 contributes to an effective defense mechanism against unauthorized access and cyber threats.
Hardware Compatibility and Upgrade Considerations
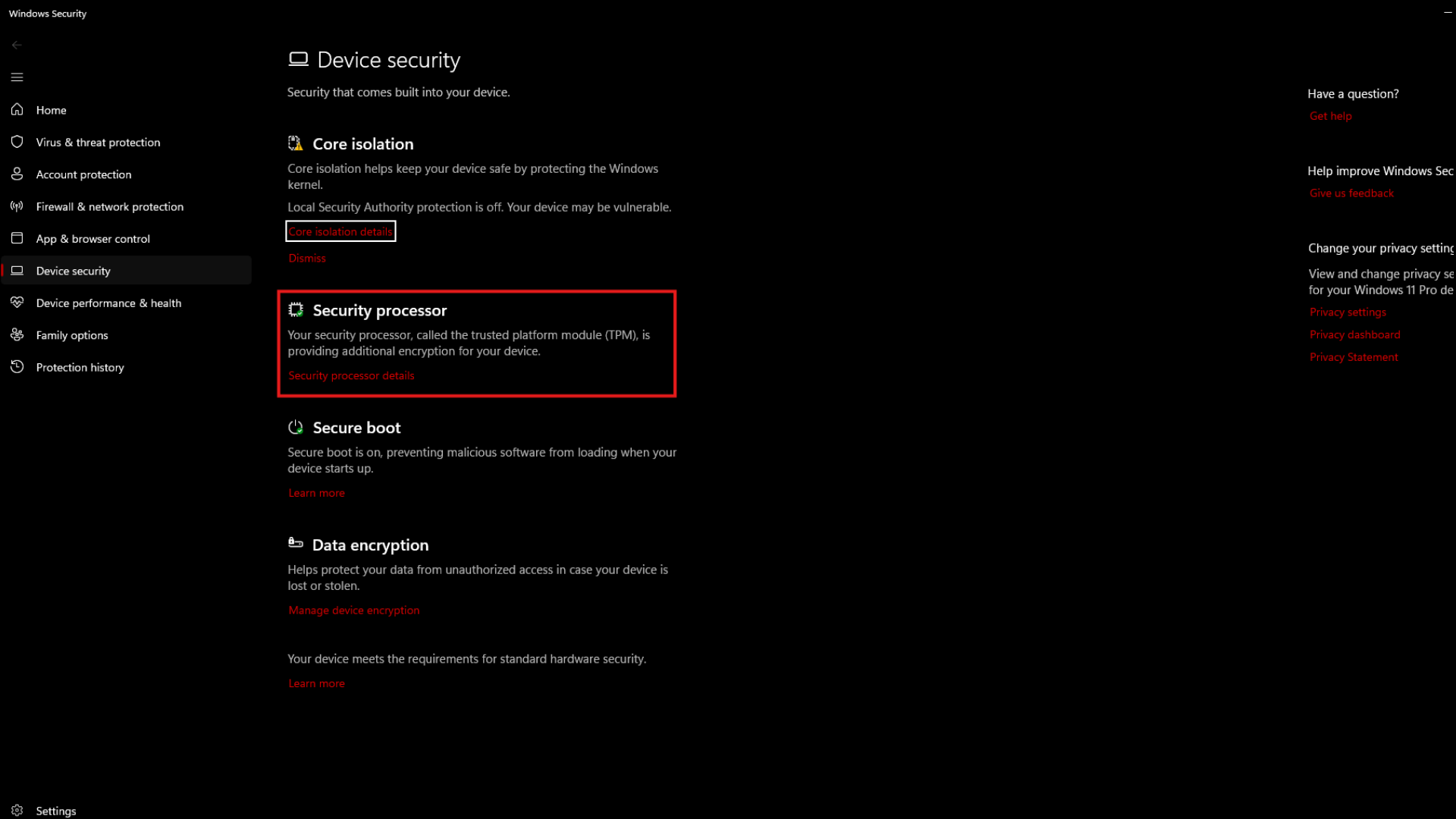
It is important to keep in mind that TPM 2.0 isn’t a software installed on your computer. It is a physical module that has been integrated into the hardware. This means that the systems that originally didn’t use TPM 2.0 cannot install it by means of a software update.
If you want to get TPM 2.0 on your computer, the only way to do so would be to upgrade from your older hardware to a modern configuration.
How to Check TPM Status on your Computer?
As we pointed out before, your system must have the hardware chip to use the feature. In case you are unsure whether your device meets this requirement, here are the steps you can follow:
For Microsoft Intune
- Launch the Intune Portal.
- Head over to ‘Devices’, and then, ‘All devices’.
- From the list of devices, select the one you want to check.
- Open the device ‘Properties’.
- Navigate to ‘Hardware’.
- You will be able to find TPM information in the ‘Security’ section.
For Microsoft Configuration Manager
- Boot up the Configuration Manager console.
- Locate ‘Assets and Compliance’, then head over to ‘Overview’.
- Open ‘Device Collections’.
- Select the desired device collection.
- Choose a device and select ‘Start’, then ‘Resource Explorer’.
- When in the Resource Explorer, expand ‘Hardware’ > ‘Security’ > ‘TPM’.
- Here, you can find the TPM resource for version information and status.
Microsoft’s Intentions with TPM 2.0
While TPM 2.0 seems like a must-have upgrade, we should discuss what Microsoft’s intentions are with it. There are two ways to go about it. Firstly, you can speculate that Microsoft mandated the feature to force users to upgrade their older but still capable setups to drive up sales.
Secondly, you can consider that Microsoft has genuinely introduced TPM 2.0 as essential for model encryption methods and secure boot processes. The system gains an additional layer of security that is less susceptible to software-based vulnerabilities.
Here is Microsoft’s statement on TPM 2.0’s present and future use-case:
Today. From supporting more intricate encryption algorithms to adding cryptographic functionality, TPM 2.0 is essential to counteracting present-day cyber risks. As such, you should not disable TPM checks on Windows 11 endpoints. Using TPM functionality for hardware-based endpoint security and Zero Trust offers organizations a powerful tool to mitigate significant security risks and potential data breaches.
Tomorrow. TPM 2.0 also helps future-proof Windows 11. One way it does so is by helping to protect sensitive information as more AI capabilities come to physical, cloud, and server architecture. The long-term benefits of enhanced security contribute to more than one of your compliance goals. It prepares you for evolving regulatory standards and industry best practices.
By instituting TPM 2.0 as a non-negotiable standard for the future of Windows, we elevate the security benchmark. It allows you and us to better align with the growing need for formidable data protection in the modern digital sphere.
Well, what are your thoughts on TPM 2.0 after gaining knowledge on the same? Do you think it should be compulsory in modern computers?
Looking For More Related to Tech?
We provide the latest news and “How To’s” for Tech content. Meanwhile, you can check out the following articles related to PC GPUs, CPU and GPU comparisons, mobile phones, and more:
- 5 Best Air Coolers for CPUs in 2025
- ASUS TUF Gaming F16 Release Date, Specifications, Price, and More
- iPhone 16e vs iPhone SE (3rd Gen): Which One To Buy in 2025?
- Powerbeats Pro 2 vs AirPods Pro 2: Which One To Get in 2025
- RTX 5070 Ti vs. RTX 4070 Super: Specs, Price and More Compared
- Windows 11: How To Disable Lock Screen Widgets
 Reddit
Reddit
 Email
Email


